SAML Integration
This document describes how to federate the Authorization service (Smart Trading Cloud) for Smart Trading Cloud services, for example, Onboarding and Testing Cloud Service, with your organization's identity provider that supports the Security Assertion Markup Language (SAML) 2.0 protocol. Thus, allowing your organization users to access Smart Trading Cloud services with the same set of credentials they use to sign in to your corporate resources.
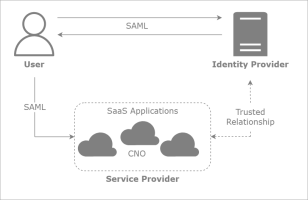
Security Assertion Markup Language (SAML) is a commonly used standardized way to tell web applications and services that a user is who he or she claims to be. SAML makes the single sign-on (SSO) scheme possible by providing a way to authenticate a user only once and then delivering that authentication to multiple applications.
After you federate the Authorization service (Smart Trading Cloud) for Smart Trading Cloud services, for example, Onboarding and Testing Cloud Service, with your organization's identity provider, at a high level, the workflow is the following:
- A payer user goes to any Smart Trading Cloud service, for example, Onboarding and Testing Cloud Service, using a web browser. The payer user is redirected to Onboarding and Testing Cloud Service sign-in screen where he/she is prompted to enter his/her email address.
- The Authorization service (Smart Trading Cloud) checks to see if the domain name of the payer user's email address has SAML federation enabled. If yes, the Authorization service sends a SAML request to the browser, which redirects the payer user to the sign-in screen of your identity provider.
- The identity provider authenticates this payer user against your organization's identity store and generates a SAML assertion that includes information about the authenticated user in the form of attributes.
- The assertion is sent to the browser that then passes this assertion to the Authorization service (Smart Trading Cloud).
- The Authorization service validates assertions' correctness, retrieves the required user attributes, and gives the payer user access to Onboarding and Testing Cloud Service.
- After successful authentication, the payer user is logged in to Onboarding and Testing Cloud Service.
Configuration Scenario
The following section demonstrates a step-by-step scenario on how to configure SAML federation for your domain.
 Also, watch the video tutorial available that shows you how to configure SAML authentication for your Smart Trading Cloud.
Also, watch the video tutorial available that shows you how to configure SAML authentication for your Smart Trading Cloud.
Prerequisites
Before you start establishing federated single sign-on for your organization account users, make sure that the following information is available:
- IdP Metadata: an XML file with your SAML identity provider metadata.
-OR-
- IdP Information:
- IdP SSO URL: The single sign-on endpoint of your identity provider to which a browser redirects a user to sign in.
- IdP Logout URL: The remote logout URL where the identity provider will send logout requests and responses. The Authorization service (Smart Trading Cloud) will redirect users to this URL after they sign out.
- Signature Verification Certificate: Your identity provider's X.509 public key certificate that the Authorization service must use to validate assertions' correctness.
Configure SAML authentication both on the Authorization service (Smart Trading Cloud) for Smart Trading Cloud services, for example, Onboarding and Testing Cloud Service, and on the identity provider sides.
To configure SAML federation for a domain:
- Go to the Authorization service at https://auth.sandbox.kollab.link and sign in as an account administrator. (
 Watch also the video tutorial available that shows you how to get started with Smart Trading Cloud.)
Watch also the video tutorial available that shows you how to get started with Smart Trading Cloud.)
- Go to the User Registrations page (
 on the left navigation bar).
on the left navigation bar).
- In Domain Management, on the tile with the required domain, click Configure Domain (
 ).
).
- Click Configure SAML Federation.
- Review the caution message on SAML support by on-premise Edifecs products. If it is not applicable for your account users, click Continue.
- In SAML Federation Configuration, in Status, after you fill out the required fields below and register Onboarding and Testing Cloud Service as a service provider in your identity provider, enable SAML federation settings for all account users or only for administrators.
- Provide IdP information either through:
IdP Metadata: Click Upload IdP Metadata to upload XML file with your SAML identity provider metadata.
-OR-
The following:
- IdP SSO URL: Select Use HTTP-POST binding for authentication requests and/or Use HTTP-POST binding for response if you want the SAML protocol messages to be transferred within the base64-encoded content of an HTML form control. If not selected, the HTTP Redirect binding is used.
- IdP Logout URL: Select Use HTTP-POST binding for logout if you want the logout messages to be transferred within the base64-encoded content of an HTML form control. If not selected, the HTTP Redirect binding is used.
- Signature Verification Certificate
- In Username (Email) Source, for the Authorization service (Smart Trading Cloud) to extract the identity of the authenticated user from the SAML assertion, specify the location of the user name (email) in the assertion that the identity provider will send as a response.
- Select Assertion subject if a user name will be located in the <saml:Subject> element of the response.
- Select Assertion attribute if a user name will be located in the <saml:Attribute> element of the response. In User Email - Attribute Name, enter the value of the attribute Name (for example, urn:oid:0.9.2342.19200300.100.1.3). Select Use attribute friendly name for the Authorization service to rely on the human-readable form of the attribute.
- In Required Attributes, specify how the attributes will be labeled in assertions. When users are logged into their personal Onboarding and Testing Cloud Service accounts, they can see their first and last names in their profile information. For this, the identity provider must send this information to the Authorization service (Smart Trading Cloud) in the form of attributes. For the Authorization service to recognize these attributes, they should be specified how to be labeled in assertions.
- In User First Name - Attribute Name, enter the value of the attribute Name that carries the user's first name (for example, urn:oid:2.5.4.42). Select Use attribute friendly name for the Authorization service to rely on the human-readable form of the attribute.
- In User Last Name - Attribute Name, enter the value of the attribute Name that carries the user's last name (for example, urn:oid:2.5.4.4). Select Use attribute friendly name for the Authorization service to rely on the human-readable form of the attribute.
- Click Save.
Service provider metadata
In the Authorization service (Smart Trading Cloud), you can download the saml-conf.xml file with the service provider metadata. To do this, click Smart Trading Cloud SAML SP Metadata.
To configure SAML federation for your identity provider:
- Go to your identity provider settings and add Onboarding and Testing Cloud Service as a service provider using the metadata (the saml-conf.xml file) (consult your identity provider documentation on how to set up a new trusted application).
- (As a last step of this configuration scenario) Go back to SAML Federation Configuration in the Authorization service. To enable SAML federation, in Status, select one of the following:
- Enable for Administrators: Only account administrators will be able to authenticate with the identity provider. They will be able to sign in using their Smart Trading credentials as well.
- Enable for All Users: All the account users (including administrators) will be required to authenticate with the identity provider. The administrators will be able to sign in using their Smart Trading credentials as well.
An then click OK.
Single Sign-on (SSO)
The following workflow occurs when single sign-on is enabled.
Single sign-on enabled
- A user goes to any Smart Trading Cloud service, for example, Onboarding and Testing Cloud Service, using a web browser. The user is redirected to the Identity Provider’s sign-in screen.
- The user enters credentials.
- The Identity Provider authenticates the user's credentials and redirects the user to the Onboarding and Testing Cloud Service home page.
Note Currently single sign-on (SSO) is not available for your partners. To access Onboarding and Testing Cloud Service, they should use the partner portal URL .
Single sign-on disabled
- A user goes to any Smart Trading Cloud service, for example, Onboarding and Testing Cloud Service, using a web browser. The user is redirected to Onboarding and Testing Cloud Service sign-in screen where they are prompted to enter their email address.
- The user is redirect to the next page to enter the password.
- After successful authentication, the user can use Onboarding and Testing Cloud Service.
Warning Edifecs do not recommend that you enable SAML authentication if your account users work with the Smart Trading Cloud artifacts through the following on-premise Edifecs applications:
- Edifecs Application Manager (version 9.2.3.1 or earlier)
- XEngine (version 9.2.3.1 or earlier)
- SpecBuilder (version 9.2.3 or earlier)
- XES Module for FHIR (version 9.2.3.1 or earlier)
 on the left navigation bar).
on the left navigation bar).  ).
).


